Pig butchering scams, which are long-con frauds that combine romance, social engineering, and counterfeit crypto platforms, have industrialised into one of the most pervasive financial threats of 2025. Once relegated to isolated incidents, these schemes now operate as global criminal enterprises, leveraging synthetic identities, deepfake media, and cross-chain laundering strategies. As enforcement tightens, adversaries evolve, exploiting regulatory gaps, new stablecoins, and decentralised infrastructure. This insight explores the latest scam architectures, laundering typologies, and technical detection strategies relevant to AML, compliance, and threat-intelligence professionals.
Threat evolution
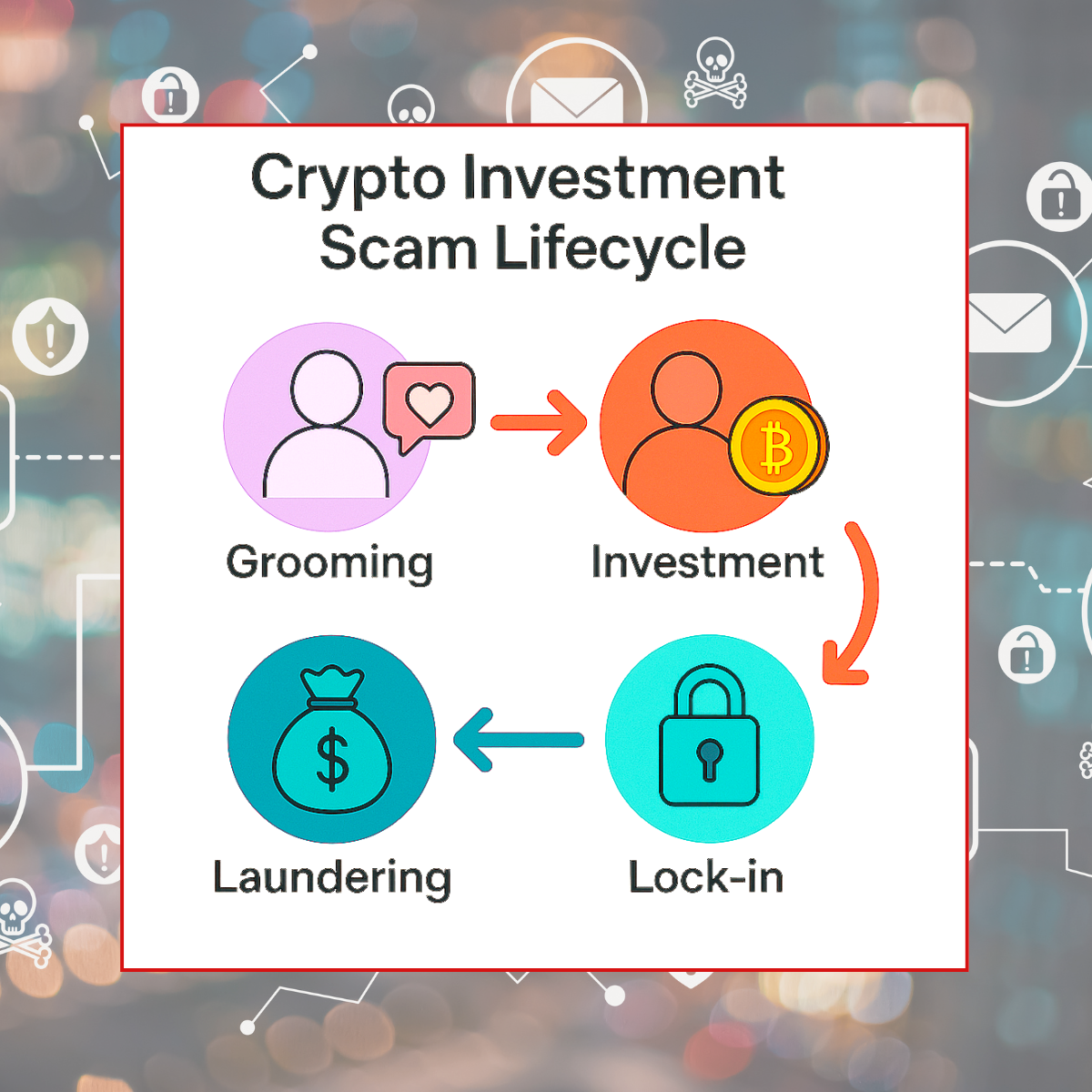
Pig butchering scams have grown from isolated romance-investment con games into full-scale criminal ecosystems. Syndicates now operate from scam compounds across Southeast Asia, Sub-Saharan Africa, and the Middle East. These centres rely on trafficked labour, fraudulent KYC onboarding, and decentralised technologies to attract, groom, and defraud victims globally.
Fraudsters build emotional trust via social platforms, later transitioning the conversation to fake crypto platforms where victims are manipulated into investing ever-increasing sums. These schemes often exploit deepfake identities and generative chatbots, offering fabricated dashboards and simulated earnings. When the victim attempts a substantial withdrawal, access is denied or blocked with fraudulent justifications. Shame and psychological manipulation frequently deter victims from reporting losses, contributing to significant under-reporting and delayed detection.
Laundering infrastructure
Once assets are extracted, stolen funds are rapidly laundered through sophisticated crypto infrastructures. Common typologies include:
- Pooling assets into self-hosted wallets
- High-speed chain-hopping using bridges and wrapped tokens
- Conversion into low-friction stablecoins like USDT on the TRON network
- Final liquidation via OTC brokers, money mule accounts, or under-regulated exchanges
In 2025, scammers increasingly adopt emergent stablecoins (e.g., rouble-pegged tokens) and semi-regulated DeFi services to bypass traditional traceability. These laundering flows often traverse multiple jurisdictions and exploit weak enforcement of Travel Rule obligations.
Detection and red flags
Traditional rule-based transaction monitoring often fails to distinguish between a scam victim and a high-risk actor. Key detection considerations for compliance teams include:
- Sudden behavioural deviation (e.g., large crypto purchases from traditionally low-risk customers)
- Transfers to unknown unhosted wallets shortly after onboarding
- Reuse of transactional descriptors and merchant endpoints across victim accounts
- Clusters of ephemeral wallets converging on known laundering hubs
In 2025, the integration of behavioural analytics, cross-chain forensic tools, and Travel Rule metadata is critical. A move from address-centric to actor-centric monitoring enables earlier interdiction and more accurate attribution.
Regulatory response
The regulatory landscape is adapting. FATF’s 2025 update prioritises typologies such as romance-investment fraud, stablecoin abuse, and the exploitation of cross-chain bridges. In parallel, Travel Rule enforcement is expanding, and initiatives like the EU’s AMLA (Anti-Money Laundering Authority) are harmonising supervision across VASPs.
October 2025 marked a turning point: coordinated sanctions from the U.S., U.K., and international partners dismantled a Southeast Asian network tied to over $4 billion in illicit flows. Designated under Section 311, several entities were cut off from the global financial system. The crackdown exposed the intersection of financial crime and human trafficking, with thousands of coerced individuals operating scam infrastructure.
Why it matters
Pig butchering frauds uniquely test the limits of AML controls, blending genuine customer behaviour with exploitative manipulation. The victims may present as legitimate investors, masking underlying duress. Financial institutions, if unable to distinguish between a scam victim and a bad actor, risk either enabling laundering or revictimising clients.
Moreover, these scams reveal the brittleness of existing KYC and onboarding safeguards. Synthetic identities, AI-generated profiles, and remote onboarding tools are now routinely exploited by industrial-scale scammers. As fraud techniques and laundering methods converge, institutions must adopt a unified fraud-fincrime intelligence strategy, blending behavioural detection, technical telemetry, and cross-platform red flag sharing.
Strategic implications
Pig butchering frauds present a uniquely hybrid threat combining psychological manipulation, technical obfuscation, and transnational laundering. Institutions must consider:
- Updating risk models to reflect “fattening” patterns: gradual increase in exposure driven by scam coercion
- Training staff on identifying long-con fraud indicators and cross-departmental escalation procedures
- Leveraging Travel Rule metadata and behavioural forensics for triangulating suspicious activity
- Participating in intelligence-sharing consortia to track scam wallet clusters and infrastructure domains
- Proactively engaging victims and integrating trace-and-freeze protocols into customer support workflows
Outlook
As policy coordination and enforcement increase, scammers are pivoting to new geographies, stablecoins, and scam front-ends (e.g., AI-generated advisors, play-to-earn covers). The combination of scalable human manipulation and decentralised financial infrastructure will continue to challenge traditional controls. Financial institutions that implement proactive, multi-layered defences, rooted in behavioural monitoring, entity risk intelligence, and international collaboration, will be best positioned to disrupt these scams.
Our perspective
At Toralya, we view pig butchering as a signal crime, an indicator of how scalable trust manipulation has become in a decentralised financial world. The convergence of synthetic identity, social engineering, and untraceable value movement represents a blueprint for future hybrid-financial threats. Defeating such threats requires a multi-domain response: compliance teams need deeper telemetry, regulators need cross-border cohesion, and investigators need shared intelligence that bridges both fiat and crypto ecosystems.
Pig butchering is not an edge case. It’s a stress test for how modern AML systems identify real victims, attribute risk, and uphold trust. Institutions that learn to solve for it now will be the ones prepared for the AI-driven, relationship-engineered fraud threats of the next decade.
Toralya Insight This analysis draws on findings from two dedicated modules within Toralya’s recent threat intelligence reporting. We explore the strategic and technical dimensions of pig butchering fraud both in:
- From Infostealer to Real Leak: What Hackers Really Sell in 2025 (Q4 Intelligence Report), and
- Crypto Threat Intelligence, Digital Forensics and AML Risk in Singapore – October 2025
📥 Download the Executive Summary: https://payhip.com/b/vDU8Q
🌐 Visit the full landing page: https://lnkd.in/deiwC7H7
🎯 The full report will be available in just 30 early-bird copies
🗓️ From 4 to 14 November 2025
💬 Enquiries and early reservation: info@toralya.io
Sources:
- Financial Action Task Force (FATF). “Targeted Update on Implementation of FATF Standards on Virtual Assets and Virtual Asset Service Providers”, June 2025.
- Financial Crimes Enforcement Network (FinCEN). “Alert on Romance Investment Scams and Pig Butchering Typologies”, FIN-2023-Alert005, September 2023.
- Financial Crimes Enforcement Network (FinCEN). “Finding that Huione Group is a Primary Money Laundering Concern”, October 2025.
- U.S. Department of the Treasury. “Joint Sanctions Against Transnational Pig Butchering Syndicates”, October 2025.
- TRM Labs. “Crypto Crime Trends and Stablecoin Laundering Q3 2025”, October 2025.
- Chainalysis. “2025 Crypto Crime Midyear Update”, August 2025.
- European Banking Authority (EBA). “Crypto-Asset Risks in the EU Financial Sector”, October 2025.
- Europol. “Human Trafficking in Cyber Scam Compounds: Emerging Geographies”, September 2025.
- Toralya. Crypto Threat Intelligence, Digital Forensics and AML Risk in Singapore, Strategic Report, October 2025.
No responses yet